
While chatting with my son, Connor, recently, he mentioned he was writing a blog post about “IoTbots” for his site. You can check out Connor’s blog here. Intrigued by the topic, I dedicate this week’s post to exploring IoT botnets. IoT botnets are networks of compromised Internet of Things (IoT) devices infected with malware and remotely controlled by malicious attackers. Their impact is growing in industrial automation.

One striking example of the risks involved occurred in February 2025, when a cybersecurity researcher discovered an unprotected database containing an astonishing 2.7 billion records, totaling 1.17 terabytes of sensitive IoT data.
The breach was traced back to Mars Hydro, a manufacturer of smart grow lights and agricultural equipment. The exposed database included:
– WiFi network names (SSIDs) and passwords
– IP addresses and unique device identifiers
– Operating system details of connected devices
– API tokens and diagnostic error logs
This level of exposure could have allowed cybercriminals to access smart farming systems, infiltrate home networks, or even compromise critical infrastructure. The root cause was a database left completely unprotected, without password security. Although Mars Hydro acted swiftly to contain the breach once notified, it remains unclear how long the data was exposed or whether unauthorized access occurred.
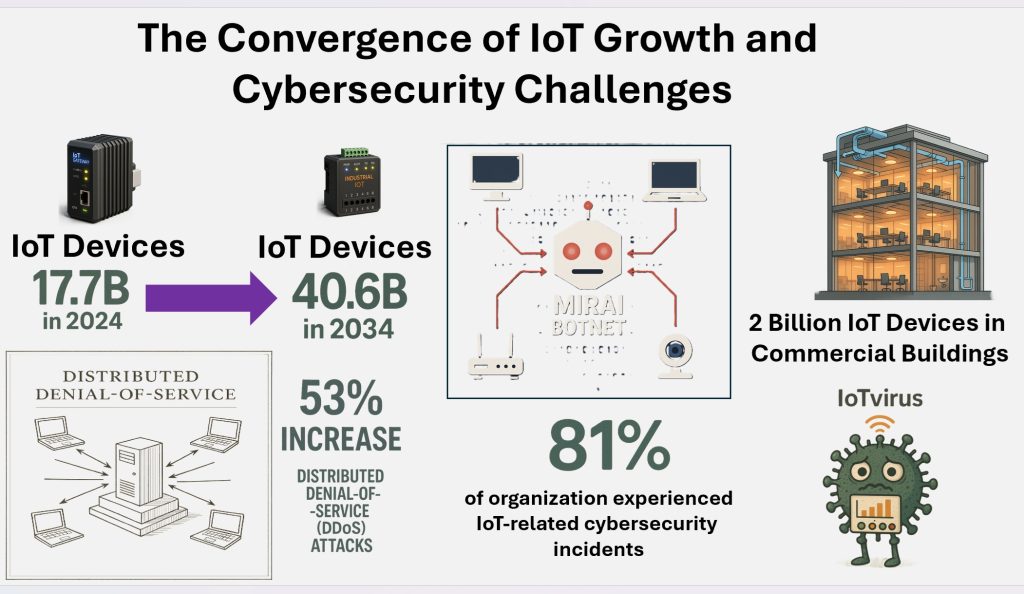
The scale and frequency of such threats are increasing in tandem with the rapid expansion of IoT. According to a report by Transforma Insights, there were 17.7 billion active Internet of Things (IoT) devices worldwide as of the end of 2024. That number is projected to reach 40.6 billion by 2034, with a compound annual growth rate (CAGR) of 9%. Annual IoT device sales are expected to double over the same period, increasing from $4.3 billion in 2024 to $9.0 billion by 2034, with a CAGR of 8%.
In the smart building sector alone, Memoori Research reports that the installed base of IoT devices in commercial buildings was just under 2 billion by the end of 2024. That number is forecasted to reach approximately 4.12 billion by 2030, growing at a CAGR of just over 13%. These devices span across offices, retail spaces, hospitality venues, and data centers. Alarmingly, 81% of organizations in this sector reported experiencing IoT-related cybersecurity incidents, highlighting the urgent need for robust security strategies.
It is increasingly critical to secure IoT deployments at scale as they continue to expand across industries, borders, and networks. For organizations operating in industrial, remote, or high-risk environments, such as those in industrial automation, vulnerabilities not only risk data breaches but can also trigger real-world operational disruptions.
The implications for organizations deploying IoT devices in operational environments, such as energy management and building automation, are more critical than ever as these threats continue to rise. At ADISRA, we have seen this firsthand through our work with customers integrating sensors and connected systems into industrial and commercial facilities. These real-world deployments make cybersecurity not just a concern but a necessity.
That is why I was particularly intrigued when Connor mentioned the Mirai Botnet, a foundational example of how unsecured IoT devices can be weaponized at scale. Over time, Mirai has evolved, with variants now capable of targeting nearly every processor type except x86, making it even more dangerous. As I dug deeper into the topic, it quickly became clear why Mirai remains so relevant in today’s IoT landscape.
The Malware Blueprint: What Mirai Taught Us About IoT Vulnerabilities
I wanted to gain a deeper understanding of Mirai-based bots, especially considering findings from Qrator Labs’ 2024 report, which revealed a 53% increase in Distributed Denial-of-Service (DDoS) attacks compared to 2023. The report also noted a 30% rise in average monthly bot activity, along with an 8% uptick in multi-vector attacks. In this more sophisticated approach, a single target is attacked through multiple methods simultaneously. These trends underscore a growing threat landscape. So, what exactly is the Mirai Botnet, and why does it matter to industrial automation companies?
What is the Mirai Botnet?
Mirai is a type of malware that targets connected devices, particularly those within the Internet of Things (IoT) ecosystem, and turns them into a network of remotely controlled “zombie” devices, collectively known as a botnet. These compromised devices follow the commands of a botmaster (or bot herder), who may be an individual or part of an organized group, typically the threat actor responsible for creating and deploying the botnet.
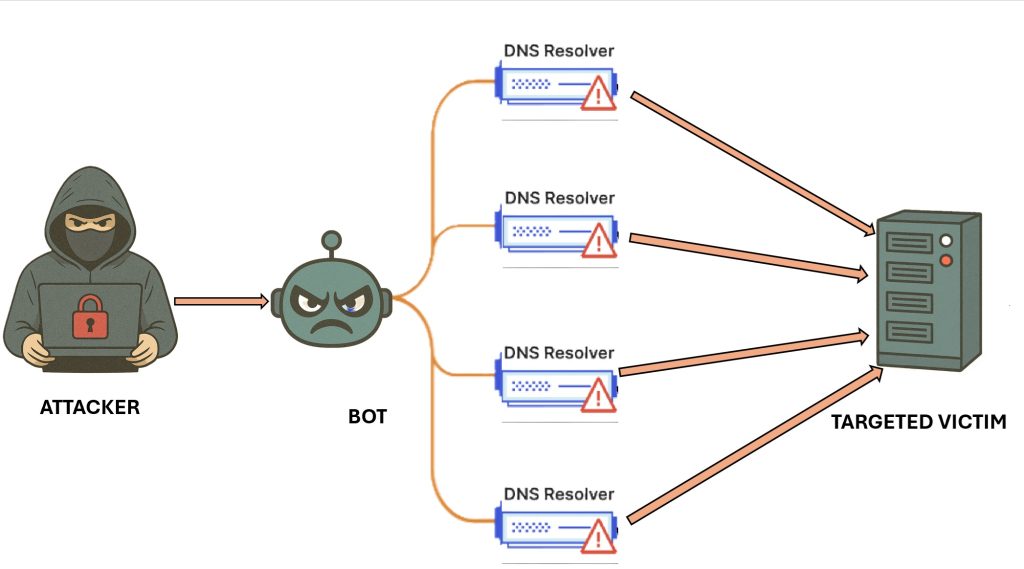
The primary objective is to infect as many devices as possible, expanding the botnet’s reach and power. These botnets are most often used to carry out DDoS attacks, which flood a server or network with traffic to overwhelm its resources and render it unavailable to legitimate users. (For more on DDoS attacks, check out our previous blog post link.)
Botnets generally follow one of two architectural models: centralized or decentralized.
In a centralized architecture, all bots communicate with one or more command-and-control (C&C) servers. When a new device is infected, it searches for the designated C&C server and connects to the botnet through it. This setup is simpler to manage but vulnerable to takedowns—disabling the C&C server can cripple the entire network.
On the other hand, decentralized (or peer-to-peer) botnets are more resilient against cybersecurity efforts and law enforcement. Without a single point of failure, these botnets can continue to operate even if part of the network is disrupted. Compromised devices communicate directly with one another, enabling the botnet to adapt and re-route commands through remaining peers.
For a deeper dive into these botnet architectures, see Barracuda’s blog link.

A Brief History of Mirai
Mirai made headlines in September 2016 when its creators used it to launch a massive DDoS attack on the website of a well-known security researcher. Just one week later, they released the source code online, likely an attempt to obscure their identity. That move backfired, as the code was quickly picked up by other cybercriminals.
In October 2016, Mirai was behind one of the most disruptive cyberattacks in internet history: the DDoS attack on Dyn, a major Domain Name System (DNS) provider. The attack peaked at an unprecedented 1 terabit per second, with some estimates reaching 1.5 terabits per second, and was fueled by the Mirai botnet, which exploited thousands of insecure Internet of Things (IoT) devices. By hijacking over 100,000 IoT devices, the attackers crippled Dyn’s infrastructure, rendering major websites and online services, including Twitter (now X), Netflix, Reddit, Spotify, Airbnb, Etsy, and the PlayStation Network, inaccessible to users across large portions of the internet.
How It Works
Mirai scans the internet in search of vulnerable IoT devices, particularly those running Linux-based operating systems. It was developed using ELF (Executable and Linkable Format) binaries, a standard file format for Linux and UNIX systems commonly found in the firmware of routers, sensors, and other IoT devices.
Mirai primarily targets devices that support the SSH (Secure Shell) and Telnet network protocols. SSH provides encrypted remote access to devices, while Telnet offers unencrypted terminal access. Mirai exploits these protocols by leveraging default or hardcoded credentials or by using brute-force techniques to gain unauthorized access. Devices with unchanged factory logins are particularly susceptible to infection.
Once a device is compromised, Mirai delivers its malware payload. In some cases, the malware’s executable files delete themselves after launch to avoid detection. To further obscure its operations, Mirai encrypts the communication between infected devices and its command-and-control (C2) servers or another bot, making it difficult for defenders to monitor or intercept malicious traffic.
Why It Still Matters
At first, I wondered why Connor was so interested in malware that first appeared back in 2016. But then I discovered something important: Mirai is evolving and mutating.
Although its original authors were eventually caught, the open-source release of Mirai’s code has led to a wave of new variants, each more dangerous than the last. Some of the most notable include:
– Okiru and Satori – More advanced and efficient at spreading
– Masuta and PureMasuta – The latter can exploit the HNAP vulnerability in D-Link devices
– OMG – Transforms infected IoT devices into proxies, helping attackers mask their identity
– IoTrooper, also known as Reaper. Reaper can compromise devices at a much faster rate and across a broader range of manufacturers, with greater command over infected bots.
– MooBot – This Mirai-based variant specifically targets D-Link routers, exploiting known vulnerabilities to gain control and add the devices to its botnet for malicious activities.
And more recently, Mirai-bot has been used in these variants:
– Aquabotv3 (2025) – The latest version of the Mirai-based Aquabot has emerged with enhanced capabilities, specifically targeting Mitel SIP phones. One of its most notable new features is its ability to report back to its command-and-control (C2) server when a kill signal is detected on an infected device, indicating increased resilience and situational awareness.
– Murdoc Botnet (2025) – These variant exploits vulnerabilities targeting AVTECH Cameras and Huawei HG532 routers.
What You Can Do About Mirai: Practical Steps to Secure IoT Devices
In today’s hyper-connected world, both consumers and manufacturers of IoT devices need to take a proactive approach to cybersecurity. The first step in strengthening your security posture is asking a fundamental question: What exactly am I protecting? When it comes to IoT, the answer is often your network perimeter—whether it spans multiple sites or exists within a single facility.
To get a practical perspective, I turned to Connor and asked what steps he recommends. Here’s what he shared:
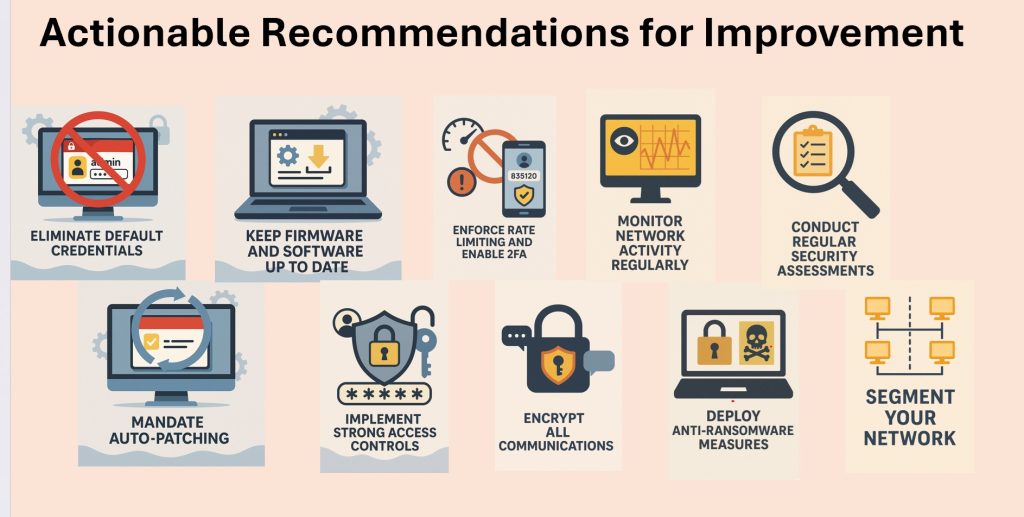
1. Eliminate Default Credentials
One of the easiest ways to harden your devices is by removing factory-default usernames and passwords. Mirai exploited these defaults to build massive botnets. Replacing them with strong, unique credentials blocks this attack vector.
2. Mandate Auto-Patching
IoT devices are often “set and forget,” making manual updates rare. Enabling automatic patching ensures vulnerabilities are fixed without user intervention. Consider the 2016 Deutsche Telekom incident, where 900,000 customers lost internet access due to unpatched routers. Do not let history repeat itself.
3. Keep Firmware and Software Up to Date
Many IoT devices run outdated or unsupported software, leaving them exposed. Regularly check for firmware updates and apply them as soon as they are available. This includes routers, which are frequent targets in large-scale attacks.
4. Implement Strong Access Controls
Use continuous authentication and authorization protocols to tightly control which devices are allowed to communicate within your network. This helps prevent unauthorized access and lateral movement by attackers.
5. Enforce Rate Limiting and Enable 2FA
Rate limiting login attempts reduces the risk of brute-force attacks. If your devices support it, enable two-factor authentication (2FA) to add another layer of defense, especially for web-based admin portals.
6. Encrypt All Communications
Ensure all data transmitted by IoT devices is encrypted. Use secure transport protocols in operational technology (OT) environments to protect sensitive data from interception or tampering.
7. Monitor Network Activity Regularly
With exposed Wi-Fi credentials and IP addresses, attackers may attempt remote access. Periodically review your router’s admin console to check connected devices. If something unfamiliar shows up, remove it immediately and update your Wi-Fi credentials.
8. Deploy Anti-Ransomware Measures
Use endpoint protection software and maintain regular off-site backups of OT systems. These practices help minimize damage from ransomware attacks targeting critical infrastructure.
9. Conduct Regular Security Assessments
Frequent audits of your IoT infrastructure help identify vulnerabilities before they can be exploited. Incorporate penetration testing and vulnerability scans into your maintenance routines.
10. Segment Your Network
Avoid converging IT and OT systems without proper isolation. Lack of network segmentation allows attackers to move laterally from less secure IT systems into critical OT infrastructure. Create clear separations to narrow potential attack surfaces.
As Connor reminded me, the security threat landscape is constantly evolving, and the strategies we use to combat today’s botnets may need to adapt tomorrow. That is why staying informed and vigilant is so important.
By following these best practices, ADISRA customers and the broader industrial automation community can take proactive steps to reduce the risks posed by Mirai and its ever-evolving variants. In the age of intelligent, connected devices, cybersecurity is not a one-time task; it is an ongoing commitment.
Your Security, Our Priority
At ADISRA, securing IIoT environments is a top priority, especially as many of the industrial devices we support run on Linux-based platforms. As OT and IT systems continue to converge in smart buildings and industrial settings, a zero-trust approach, with strong authentication, least privilege access, and real-time anomaly detection, is essential to safeguarding operations.
We are committed to staying ahead of this evolving threat landscape. If you are deploying IoT or OT systems and want a modern HMI/SCADA solution built with these challenges in mind, we invite you to try ADISRA SmartView. Contact us today to schedule a demo or initiate your evaluation.

Interested in our next webinar on Rule-based Expert Systems?
Join us for our upcoming webinar on June 24th at 9:30 AM CDT to explore how the built-in rule-based expert system in ADISRA SmartView transforms alarm management, diagnostics, and decision-making on the plant floor.
Webinar Title:
From Rules to Results: Harnessing the Power of Rule-Based Expert Systems in ADISRA SmartView
Discover how to transition from reactive operations to proactive performance with intelligent automation tools.
Register for the webinar here.
ADISRA®, ADISRA’s logo, InsightView® and KnowledgeView® are registered trademarks of
ADISRA, LLC.
Copyright
© 2025 ADISRA, LLC. All Rights Reserved.
