
Blog written by Connor Gadbois and Marcia Gadbois
In today’s rapidly evolving industrial landscape, the convergence of the Industrial Internet of Things (IIoT), digital transformation, and enhanced supply chain connectivity redefine how businesses operate and collaborate with suppliers and customers. This heightened connectivity while unlocking unprecedented opportunities for efficiency and innovation, also amplifies the critical need for robust cybersecurity. Organizations that thrive in this new era will place cybersecurity at the heart of their transformation strategies, ensuring it is not merely a technical concern but a fundamental aspect of their organizational culture. Success will depend on executives and cross-functional IT/OT teams working together to develop and enforce proactive cybersecurity strategies, embedding security as a shared responsibility throughout the enterprise.
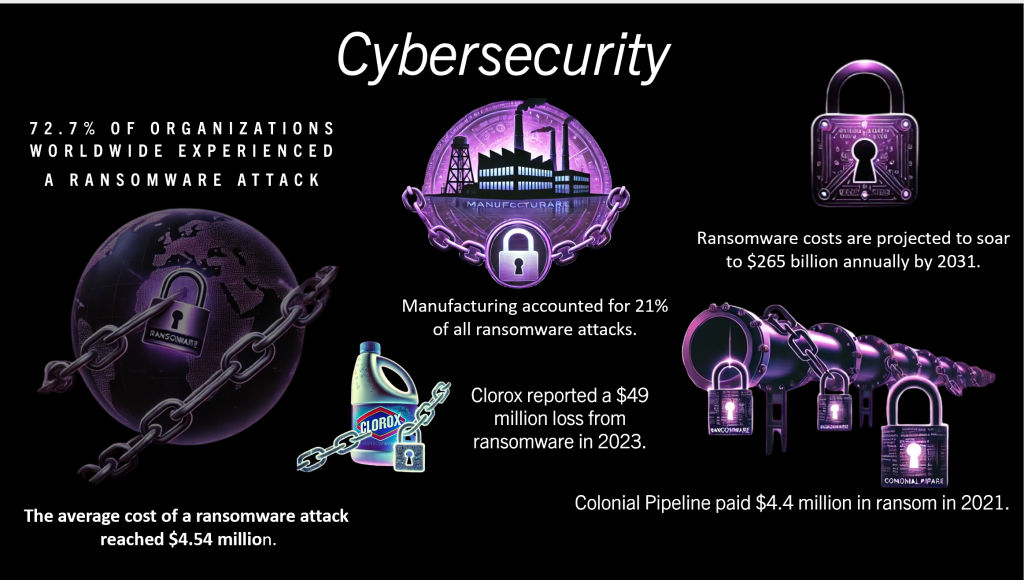
In 2023, a staggering 72.7% of organizations worldwide experienced a ransomware attack, highlighting the growing prevalence of this cyber threat. The financial impact is equally alarming, with ransomware costs projected to soar to $265 billion annually by 2031, a sharp increase from $20 billion in 2021. The average cost of a ransomware attack reached $4.88 million, while the cost of recovery alone, excluding ransom payments, averaged $1.82 million, underscoring the substantial economic burden ransomware imposes on businesses globally.
According to an analysis by Black Kite, reported in InfoSecurity Magazine on October 2, 2024, manufacturing was the top target for ransomware groups between April 1, 2023, and March 31, 2024. During this period, manufacturing accounted for 21% of all ransomware attacks, with 1,016 out of 4,893 victims in this sector. Ransomware is malicious software that encrypts a victim’s data, rendering it inaccessible and demanding a ransom payment for its decryption or restoration. Such attacks can paralyze critical systems, causing severe operational and financial damage. Below are two of the most notable ransomware incidents from recent years:
Colonial Pipeline (May 2021)
The Colonial Pipeline ransomware attack targeted critical infrastructure supplying gasoline and jet fuel to the U.S. East Coast. The attackers, linked to the DarkSide ransomware group, infiltrated the company’s systems and encrypted their data. This forced Colonial Pipeline to shut down its operations, resulting in widespread fuel shortages and panic buying. The incident highlighted the devastating impact ransomware can have on essential services.
Clorox (August 2023)
The ransomware attack on Clorox disrupted production and operations for the major consumer goods company. The cyberattack compromised key IT infrastructure, forcing the company to process orders manually, causing delays, and an inability to meet consumer demand. The attack resulted in $356 million in damages, slowed order processing, and product shortages on store shelves, revealing significant vulnerabilities in Clorox’s cybersecurity defenses.
These examples underscore the urgent need for robust cybersecurity measures, particularly for industries that form the backbone of critical infrastructure and consumer supply chains.
Why Is Manufacturing a Prime Target for Ransomware?
Manufacturing is a prime target for ransomware attacks due to the sensitive data it handles, including customer information, production plans and designs, financial records, and intellectual property such as trade secrets. This wealth of critical information makes this sector an attractive target for cybercriminals.
Additionally, manufacturing relies on complex, interconnected systems to operate efficiently. Picture a plant with automated robots, computer-controlled machines, and real-time data analytics—all of which depend on seamless interconnectivity. Any disruption to these interconnected systems can halt operations and lead to significant financial losses, making manufacturers particularly vulnerable to cyberattacks.
Another contributing factor is the widespread use of legacy systems in manufacturing. Many of these systems run outdated software or operating systems that are no longer supported by vendors. While these systems are often integral to production processes and challenging to replace, they pose a significant cybersecurity risk due to the lack of modern security updates and patches.
Furthermore, the relentless pressure to maintain production efficiency and meet customer demands can overshadow cybersecurity priorities. Under constant deadlines, manufacturers may delay critical software updates, forego regular security audits, or neglect employee training on cybersecurity best practices—all of which increase their vulnerability to attacks.
Manufacturing organizations must shift their mindset and embed cybersecurity into their organizational culture to address these risks. Executives and cross-functional teams from both IT and OT must work together to develop and enforce comprehensive cybersecurity strategies, ensuring security becomes a shared responsibility across all levels of the organization.

Foundational Principles for Strengthening Cybersecurity
In an era where cyberattacks and data breaches are escalating, protecting your organization from hackers is more critical than ever. Cybersecurity extends far beyond the capabilities of a single software package; it requires a comprehensive architecture built on key principles. These foundational concepts will enhance the recommendations provided in the subsequent sections on best practices for cybersecurity and cloud security. Below are the essential principles to consider:
1. Defense in Depth
Think of this as creating an obstacle course for cybercriminals. Defense-in-depth is a strategy that employs multiple layers of security controls to protect systems and data. Rather than relying on a single security measure, this layered approach increases resilience and reduces the likelihood of a single point of failure. If one layer is breached, others remain in place to maintain security. This approach ensures failures occur safely, effectively mitigating risks.
2. Least Privilege
The principle of least privilege dictates that individuals should only have the access rights necessary to perform their specific tasks and only for as long as required. Restricting unnecessary access minimizes exposure to potential threats. Regular reviews should be conducted to ensure that permissions are still justified, reducing the risk of unauthorized access.
3. Separation of Duties (SoD)
Separation of duties aims to minimize the risk of fraud, data theft, and security breaches by dividing critical tasks among multiple individuals. By ensuring no one person has full control over a process or system, this principle requires collusion for malicious activity to succeed, making it significantly harder to exploit vulnerabilities.
4. Secure by Design
“Secure by Design” emphasizes integrating security into every stage of a system or product’s development, from planning to deployment. This proactive approach ensures that security is not an afterthought but a fundamental element, reducing vulnerabilities and making systems more resilient to attacks.
5. Keep It Simple (KISS)
Effective security plans must be simple enough for everyone in the organization to follow. Overly complex systems can discourage adherence, leading to mistakes or deliberate circumvention. By keeping security measures straightforward yet robust, organizations can make it easier to do the right thing than the wrong, fostering better compliance and overall security.
By embedding these principles into your cybersecurity architecture, you can create a resilient framework that minimizes risks and strengthens your organization’s defense against evolving threats.

Best Practices in Cybersecurity: Building a Resilient Defense
In today’s hyperconnected world, the stakes for cybersecurity have never been higher. With increasing reliance on digital systems, cloud platforms, and interconnected devices, the risk of cyberattacks continues to grow exponentially. Businesses of all sizes face threats ranging from data breaches to ransomware attacks that can disrupt operations, damage reputations, and result in significant financial losses. Implementing robust cybersecurity best practices is no longer optional—it is essential for survival in this digital age. This section outlines key strategies and actionable steps organizations can adopt to fortify their defenses, safeguard sensitive data, and ensure business continuity in the face of ever-evolving cyber threats.
1. Network Segmentation
Implementing network segmentation is a key cybersecurity strategy to protect Industrial Control Systems (ICS) and critical operational infrastructure. By separating ICS from other networks and introducing multiple layers of security, organizations can significantly reduce potential attack surfaces and contain breaches more effectively. Bridging the gap between IT and OT networks is also vital to safeguarding critical infrastructure, ensuring both systems can coexist securely without compromising each other.
For high-value operational infrastructure, air-gapping provides an added layer of protection. By physically isolating critical systems from any network connected to the internet, organizations can prevent remote attacks—even when outdated software is in use. This isolation ensures that operational systems remain secure and resilient against external threats.
2. Regular Security Assessments and System Hardening
Conducting regular vulnerability assessments and penetration testing is essential for identifying and addressing potential weaknesses in your systems. Staying informed about vulnerabilities in the software you are running is one of the simplest yet most effective ways to detect and fix issues before they can be exploited by attackers.
In addition to assessments, system hardening plays a critical role in minimizing attack surfaces. For example, when installing a new software package, carefully review all the services it enables. A web server may have a default configuration that includes necessary HTTP services but might also activate FTP or SSH services for remote access. Evaluate whether these additional services are needed; if not, disable or remove them to reduce your exposure to potential threats. Every unnecessary service increases your attack surface, making your system more vulnerable.
Another crucial aspect of hardening is managing system IDs. Remove any unnecessary accounts and rename the ones you retain to avoid using default settings. For instance, if the default administrator account is named “admin,” change it to a less predictable name. Leaving systems in their default, “vanilla” configurations makes it easier for cybercriminals to exploit known settings and gain access. Proactively hardening your system ensures that attackers face significantly more resistance even if they attempt to breach it.
3. Employee Training: Strengthening the Human Firewall
Employees play a pivotal role in cybersecurity, often serving as the first line of defense against threats. However, they can also be the weakest link if not properly educated. Regular training on cybersecurity best practices is essential to help employees understand the risks, recognize potential threats and avoid falling victim to attacks such as phishing and social engineering.
Phishing emails with infected attachments remains one of the most common methods attackers use to infiltrate organizations. Spear-phishing tactics, which target specific individuals—especially those with access to critical infrastructure—are dangerous. Attackers may exploit password reuse or weak credentials to gain unauthorized access. Educating employees about these risks and how to respond to suspicious activity is crucial for reducing vulnerabilities.
Cybersecurity is not just a technology problem but a people, processes, and knowledge problem. Training employees to recognize and counter phishing attacks, social engineering tactics, and other threats empowers them to act as a robust layer of security, protecting the organization from within. Regularly reinforcing this knowledge ensures that cybersecurity awareness becomes integral to the workplace culture.
4. Access Controls: Enhancing Security Through Restriction
Implementing strict access controls is vital for preventing unauthorized access and protecting critical systems. Measures such as two-factor authentication (2FA) and adhering to the principle of least privilege ensure that only authorized personnel have access to sensitive systems and data.
Two-factor authentication adds an essential layer of security. Even if login credentials are compromised through phishing, brute force attacks, or previous breaches, 2FA acts as a barrier, preventing unauthorized access. Additionally, it provides an opportunity to detect and monitor suspicious login attempts, allowing organizations to respond proactively to potential threats.
By combining 2FA with the principle of least privilege—granting users only the access they need to perform their roles—organizations can significantly reduce the attack surface and limit the potential impact of a security breach. These measures are key components of a robust cybersecurity strategy.
5. Future-Proofing Security with Advanced Authentication and Governance
Robust authentication mechanisms, encryption protocols, and governance frameworks are becoming standard practices to safeguard critical data and future-proof applications against the rapid advancements in AI. These foundational elements are essential for ensuring resilience in an era of evolving cybersecurity threats.
The adoption of passwordless solutions, such as passkeys and biometrics, is rising. Coupled with AI-driven threat detection, these technologies streamline user experiences while enhancing security. They also enable more granular policy controls across devices, allowing organizations to enforce security measures without introducing unnecessary user friction.
While passwordless solutions reduce the burden of managing and remembering multiple passwords, they are not without risk. If a passkey or biometric credential is compromised, it could potentially grant unauthorized access to all systems tied to that single credential. This underscores the importance of layering these solutions with additional safeguards, such as multi-factor authentication and continuous monitoring, to mitigate vulnerabilities and ensure comprehensive security.
6. Incident Response Plan: Prepare for the Unexpected
Developing a comprehensive incident response plan is crucial for minimizing the impact of cybersecurity breaches. This plan should clearly define communication protocols, roles, and responsibilities for all stakeholders involved. It must also outline detailed recovery procedures to restore operations swiftly and minimize downtime. A well-prepared incident response plan ensures your organization can act decisively in the face of a security incident, reducing chaos and mitigating potential damages.
7. Security Updates: Staying Ahead of Vulnerabilities
Keeping all software and hardware up-to-date with the latest security patches and firmware updates is essential to minimize vulnerabilities. Regular updates address known security flaws, reducing the risk of exploitation by cybercriminals.
Continuous system monitoring and proactive threat detection are becoming standard practices. These measures, paired with robust authentication protocols, ensure that organizations remain vigilant and prepared for emerging threats. By staying proactive with security practices, organizations can protect their critical assets and maintain resilience against evolving cyber risks.

Enhancing Cloud Security in Industrial Automation
With the increasing integration of cloud computing in industrial automation alongside traditional on-premise applications, securing cloud environments has become a critical component of organizational resilience. Cloud infrastructure plays a vital role in enabling flexibility, scalability, and real-time insights, but it also introduces unique cybersecurity challenges. Below are some best practices to strengthen cloud security and ensure the reliability of your operations.
1. Multi-Factor Authentication (MFA)
Enable MFA for all user accounts to add an extra layer of security beyond just a password. This approach helps protect against unauthorized access even if passwords are compromised. MFA can secure business operations, online transactions, banking accounts, and personal identity.
Alternate terms for MFA include:
Multi-Factor Authentication
– Two-Step Authentication
– 2-Step Verification
– Two-Factor Authentication (2FA)
Additionally, enforce strong password policies, such as requiring complex passwords with at least 12 characters, numbers, and special symbols. If using access keys under Identity and Access Management (IAM), ensure they are securely managed.
2. Data Encryption
Encrypt sensitive data both in transit and at rest. Use SSL/TLS protocols for secure data transmission and leverage encryption mechanisms provided by your cloud provider for stored data. Securely manage encryption keys to prevent unauthorized access. This principle also applies to email and other communications containing critical infrastructure information—always use HTTPS for web services.
3. Principle of Least Privilege (PoLP)
Implement the principle of least privilege and Role-Based Access Controls (RBAC) to ensure users and applications have only the permissions necessary for their tasks. Regularly review and revoke unnecessary access to reduce the risk of unauthorized activity.
4. Continuous Monitoring and Logging
Set up continuous monitoring and centralized logging for cloud resources and services. Watch for suspicious activities, unauthorized access, and anomalies. Utilize logs for incident investigation and compliance purposes. Conduct regular security audits to identify and mitigate risks and perform vulnerability scans across all systems to stay ahead of threats.
5. Automated Security and Compliance
Leverage automation for routine security tasks such as vulnerability scanning, configuration management, and compliance checks. Tools like Infrastructure as Code (IaC) can enforce consistent security configurations, ensuring secure deployments across your cloud environment.
6. Disaster Recovery Plan
Establish a robust disaster recovery plan, including frequent backups of critical resources. Use multi-region cloud hosting to replicate architecture and ensure redundancy. Regularly test your plan to verify its effectiveness in the event of a failure or attack.
Conduct vendor security assessments, requesting reports like “System and Organization Controls” (SOC). Develop a security checklist tailored to your organization’s needs to evaluate vendor reliability.
Additional Recommendations
Compromised Credentials: Since 80% of breaches result from compromised credentials, enforce strong password policies and use MFA to eliminate single points of failure.
Air-Gapped Systems: Protect outdated systems by air-gapping them from internet-connected networks. However, remain vigilant, as user interaction with these systems can still introduce vulnerabilities. Regular updates and security monitoring are essential, even for air-gapped systems.
Ransomware Defense: Implement frequent snapshots of virtual machines running critical services. This ensures quick recovery during a ransomware attack, allowing operations to continue without significant disruption.
By following these best practices, organizations can effectively manage their cloud security and ensure their operations remain resilient against evolving cyber threats.
Key Cybersecurity Standards for Industrial Automation
Numerous cybersecurity standards exist, many tailored to specific industries and applications. For organizations involved in industrial automation, adhering to the right standards is critical for safeguarding operations and ensuring compliance. Here is a quick overview of some key cybersecurity standards to watch:
- The IEC 62443 series of standards provides internationally recognized guidelines to protect Industrial Automation and Control Systems (IACS) from cyber threats. This comprehensive framework addresses cybersecurity across the entire lifecycle of these systems, including risk assessment, security policies, network protection, access control, and incident management. It is a critical standard for safeguarding industrial infrastructure.
- The Network and Information Systems Directive 2 (NIS2) is a European Union (EU) regulation designed to enhance cybersecurity across the region. It builds on the original NIS Directive by expanding the scope of covered sectors, introducing stricter compliance requirements, and imposing tougher penalties for non-compliance. The primary objective of NIS2 is to establish a high and uniform level of cybersecurity across all EU member states, ensuring more resilient and secure networks and information systems throughout the Union.
- The UK Cyber Security and Resilience Bill modernizes the nation’s cybersecurity framework, aligning with the EU’s Cyber Resilience Act. It aims to protect critical infrastructure and enhance online safety by establishing robust standards. The bill focuses on securing connected products, such as IoT devices, requiring manufacturers to design them with strong security measures. By collaborating with industry and adopting a comprehensive risk management approach, the bill seeks to bolster the UK’s cybersecurity resilience.
- The EU AI Act establishes regulations for the development, deployment, and use of artificial intelligence (AI) systems across the European Union. A critical component of the legislation is its emphasis on cybersecurity, ensuring that AI systems are designed and implemented with robust security measures to protect users and data.
- The National Institute of Standards and Technology (NIST) develops cybersecurity standards, guidelines, and best practices to enhance the security of U.S. government and private organizations. Its widely adopted Cybersecurity Framework (CSF) helps organizations manage and strengthen their cybersecurity posture. The voluntary framework is adaptable to varying sizes, complexities, and industries.
Securing SCADA and HMI Systems: A Holistic Approach
SCADA (Supervisory Control and Data Acquisition) and HMI (Human-Machine Interface) systems are vital to critical infrastructure, overseeing essential operations such as power grids, water treatment facilities, and oil and gas pipelines. While these systems are crucial for maintaining modern society’s functionality, they increasingly become cyberattack targets. However, securing these systems requires more than the security features built into a single software package—it demands a holistic approach to the entire corporate security ecosystem. Ensuring the safety and security of the technology underpinning our daily services is essential to protecting critical infrastructure.
At ADISRA, we take cybersecurity threats seriously and design our products with security in mind. For more information about our solutions, visit our website at www.adisra.com.
– Try ADISRA SmartView: Download a free software trial on our website here.
– Explore InsightView and KnowledgeView: Request a temporary account to experience these powerful tools by visiting our website here.
Conclusion
The convergence of IIoT, digital transformation, and cloud integration has ushered in a new era of operational efficiency and collaboration in industrial automation. However, this increased connectivity also amplifies cybersecurity risks, making organizations need to adopt a holistic approach to cybersecurity strategies. From SCADA and HMI systems to cloud environments, securing critical infrastructure demands a blend of robust technology, proactive policies, and continuous vigilance.
Ransomware attacks, legacy vulnerabilities, and evolving threat landscapes underscore the urgent need for comprehensive security measures. Key practices such as network segmentation, regular security assessments, employee training, and multi-factor authentication can bolster defenses. Moreover, leveraging industry standards like IEC 62443, NIST CSF, and global regulatory frameworks ensures alignment with best practices and compliance requirements.
By adopting a proactive cybersecurity approach and partnering with vendors like ADISRA, we can collaboratively create a future where industrial automation thrives securely in an increasingly interconnected world.
This blog was created in collaboration with my son, Connor Gadbois, a student at Rochester Institute of Technology, where he is pursuing a degree in information technology and cybersecurity. You can connect with Connor on LinkedIn or visit his personal website here.
