By Connor Gadbois and Marcia Gadbois

The cybersecurity landscape for industrial automation will be more complex and dynamic than ever in 2025. Industrial systems are increasingly exposed to evolving threats as IT (Information Technology) and OT (Operational Technology) continue to converge, expanding the attack surface. From AI-powered cyberattacks to ransomware and supply chain breaches, malicious actors are becoming more sophisticated, persistent, and unpredictable.
Securing industrial automation environments now demands a layered, proactive strategy that combines robust security architecture, continuous threat monitoring, and comprehensive employee training.
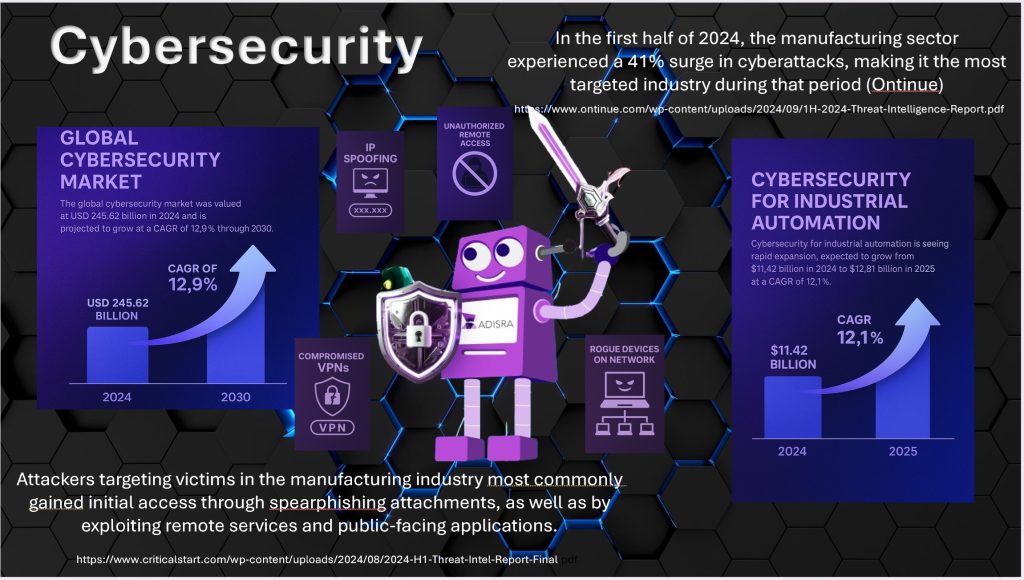
According to recent market research, the global cybersecurity market was valued at USD 245.62 billion in 2024 and is projected to grow at a CAGR of 12.9% through 2030. A key driver of this growth is the surge in cyberattacks targeting cloud infrastructure, e-commerce platforms, and smart, connected devices. In particular, cybersecurity for industrial automation is seeing rapid expansion, expected to grow from $11.42 billion in 2024 to $12.81 billion in 2025 at a CAGR of 12.1%.
Infrastructure protection represents the largest market share within this sector, highlighting the importance of securing physical and digital assets, such as transportation networks, communication systems, and operational technologies that form the backbone of modern industry.
ADISRA recognizes that cybersecurity is not just a feature; it is a foundational requirement. While our industrial software includes built-in security capabilities (as detailed in our whitepaper), proper protection depends on a secure deployment environment and a culture of cybersecurity awareness.
To support this mission, my son, Connor Gadbois, and I launched a blog series several months ago focused on industrial automation’s most pressing cybersecurity threats. We began by exploring core cybersecurity principles and best practices, followed by a deep dive into securing cloud environments. From there, we examined some of the most prevalent attack vectors, including phishing, ransomware, denial-of-service (DoS), distributed denial-of-service (DDoS), and man-in-the-middle (MitM) attacks. You can catch up on those earlier posts here.
This month, we are continuing the series by focusing on threats to network integrity: unauthorized remote access, IP spoofing, compromised VPNs, and rogue devices.
We hope these insights help you stay informed and keep cybersecurity in mind as you build and maintain your industrial automation systems.
Unauthorized Remote Access: A Leading Cybersecurity Threat in 2025
Unauthorized remote access remains a serious cybersecurity threat facing industrial automation in 2025, intensified by the rise of AI-powered attack methods. This threat involves gaining control of systems outside the network without proper authentication, often through overlooked vulnerabilities or misconfigured infrastructure.
Cybercriminals now use sophisticated tools to scan for exposed systems and quietly infiltrate networks. Common attack vectors include:
Unpatched Software Vulnerabilities – Exploiting outdated or unprotected systems.
Remote Access Trojans (RATs) – Install malicious software that grants control to attackers.
Social Engineering and Phishing – Tricking users into disclosing login credentials or clicking on malicious links.

According to CrowdStrike, 52% of observed vulnerabilities were tied to unpatched systems, emphasizing the urgent need to secure entry points before adversaries establish persistence. In the manufacturing sector, attackers often gain initial access through spearphishing emails, exploitation of remote services, and weaknesses in public-facing applications.
Why Unauthorized Access Happens
Human Factors
Employees may inadvertently aid attackers using weak passwords like password123 or fall victim to phishing scams. This is akin to unknowingly handing over the keys to your facility. A lack of cybersecurity awareness only increases this risk.
Technological Vulnerabilities
Outdated operating systems, insecure web applications, and unpatched software create exploitable weaknesses. These gaps allow attackers to bypass defenses and access sensitive data.
Inadequate Security Measures
Without strong access control, encryption, and continuous monitoring, organizations leave critical systems exposed. Think of it like a building without locks, alarms, or security personnel, making it easy for intruders to slip in unnoticed.
Sophisticated Attack Methods
Threat actors continually evolve their tactics, using AI-driven tools, ransomware, advanced phishing campaigns, and social engineering to bypass security measures and gain unauthorized access.
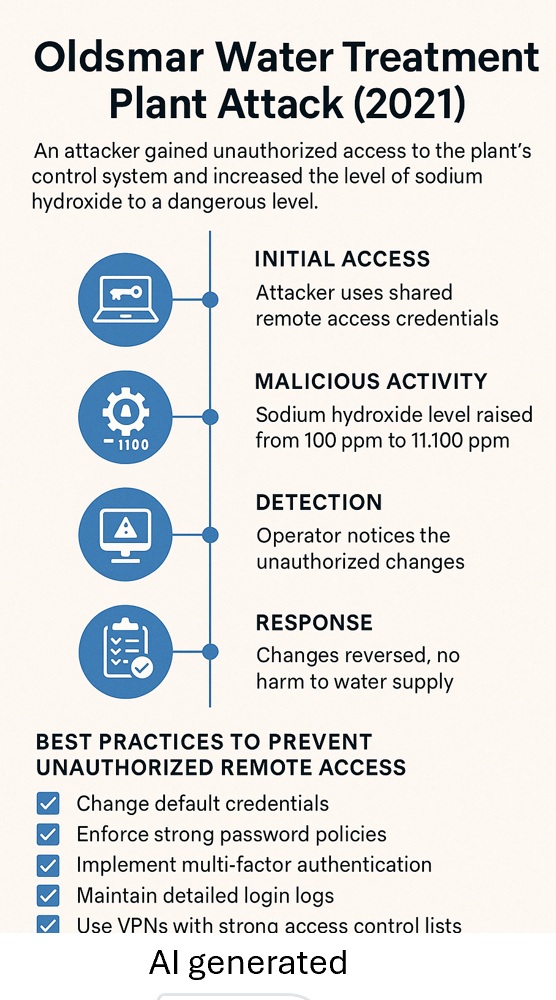
Case Study: Oldsmar Water Treatment Plant Attack (2021)
One of the most well-known cases of unauthorized remote access in industrial automation occurred at the Oldsmar water treatment plant in Florida in 2021. In this incident, an attacker gained unauthorized access to the plant’s control system and attempted to increase the level of sodium hydroxide from 100 parts per million (ppm) to a dangerous 11,100 ppm. Sodium hydroxide, while commonly used to control water acidity, becomes highly corrosive and harmful at such concentrations.
The attack was detected in real time by a plant operator who noticed the chemical levels being altered. The operator quickly reversed the changes, preventing contaminated water from reaching the city’s supply. Notably, the incident occurred just two days before the Super Bowl and only 15 miles from the stadium, heightening national concern over critical infrastructure security.
The breach was later linked to the use of shared remote access credentials among employees, highlighting the risks of poor access control practices. Although initial reports pointed to a sophisticated cyberattack, further investigation suggested a combination of human error and inadequate cybersecurity protocols. Regardless of the technical cause, the event served as a wake-up call for the vulnerabilities posed by remote access in critical infrastructure systems.
Best Practices to Prevent Unauthorized Remote Access
To reduce the risk of incidents like Oldsmar, organizations should implement the following cybersecurity measures:
Change Default Credentials
Replace manufacturer-set usernames and passwords with unique, strong credentials. Default passwords are often publicly available and exploited by attackers using automated tools. CISA has recommended eliminating default credentials in industrial control systems (ICS).
Enforce Strong Password Policies
Require complex passwords with at least 10 characters, including uppercase and lowercase letters, numbers, and special characters. Use automated systems to enforce password strength and regular updates.
Implement Multi-Factor Authentication (MFA)
MFA adds a critical layer of security by requiring two or more verification factors before granting access, significantly reducing the likelihood of credential-based attacks.
Maintain Detailed Login Logs
Logging who accessed the system, when and from where, helps detect unusual activity, such as login attempts during off-hours or from unfamiliar IP addresses. These logs support incident response, auditing, and compliance efforts.
Use VPNs with Strong Access Control Lists (ACLs)
VPNs should be configured with ACLs that restrict access based on user identity, IP address, and role. This allows only authorized users to reach sensitive systems, even within the encrypted tunnel.
Understanding IP Spoofing in Cybersecurity
IP spoofing is a cyberattack technique in which a threat actor forges the source address of Internet Protocol (IP) packets to disguise their identity, impersonate another system, or both. By manipulating this critical data, attackers can bypass basic trust mechanisms, intercept sensitive information, or launch large-scale attacks, such as the Distributed Denial-of-Service (DDoS) attacks we discussed in a previous blog.
When data is transmitted over the internet, it is broken into packets, each carrying a source and destination IP address, similar to return and delivery addresses on mail. Systems use this routing information to verify the origin of a request and whether it can be trusted. In spoofing attacks, hackers tamper with packet headers to fake the source IP, allowing them to evade detection or impersonate a trusted entity.
Why It Matters
In environments that rely on IP-based trust, sometimes called the castle-and-moat approach, devices inside the network are often trusted by default. IP spoofing exploits this assumption, making it possible to infiltrate systems that lack multi-layered authentication. As a result, more advanced and modern security strategies, such as multi-factor authentication and zero-trust architectures, are now considered essential.
Common Cyberattacks Enabled by IP Spoofing
– DDoS Attacks
Spoofed IPs amplify and direct traffic from botnets, overwhelming a server or network until it becomes unresponsive.
– Botnet Attacks
Compromised devices (bots), often masked with spoofed IPs, are remotely controlled to execute coordinated cyberattacks, including spam campaigns, data breaches, and service disruption.
– Man-in-the-Middle (MITM) Attacks
Attackers intercept communications between two parties, posing as one to manipulate or steal data. IP spoofing helps attackers remain hidden in these exchanges.

Notable Examples of IP Spoofing
– GitHub DDoS Attack (2018)
In one of the largest DDoS attacks recorded, GitHub was hit with 1.35 Tbps of spoofed traffic, knocking services offline for nearly 20 minutes. The platform mitigated the threat by redirecting traffic through a scrubbing service.
– Stuxnet (2010)
While best known for exploiting zero-day vulnerabilities in Siemens PLCs at Iran’s Natanz facility, Stuxnet also employed IP spoofing to send fake commands to industrial systems, blending in with legitimate traffic.
Other Forms of Network Spoofing
– IP spoofing is not the only way attackers deceive systems. Related spoofing techniques include:
– DNS Spoofing (DNS Poisoning) – Redirects users to malicious websites by corrupting DNS records.
– Email Spoofing – Sends emails with forged headers to impersonate legitimate sources.
– Website Spoofing – Mimics trusted websites to trick users into sharing credentials.
– ARP (Address Resolution Protocol) Spoofing – Misleads devices on a LAN by associating the attacker’s MAC address with a legitimate IP address.
– SMS (Short Message Service) Spoofing – Alters the sender ID of text messages to impersonate trusted contacts or institutions.
Mitigation Strategies and Best Practices
Organizations can reduce the risk of IP spoofing with layered security practices, including:
– Packet Filtering
Routers and firewalls should use access control lists (ACLs) to inspect packet headers and block those with suspicious or mismatched IP addresses.
– Ingress and Egress Filtering
– Ingress filtering blocks incoming packets from spoofed source IP addresses.
– Egress filtering prevents outbound traffic from using spoofed internal IP addresses.
– Strong Authentication
Avoid relying on IP addresses for authentication. Use secure, multi-factor methods to verify user identity for all remote access.
– IP-Level Encryption
Use encrypted protocols (e.g., IPsec) to protect communication, preventing attackers from reading or spoofing IP addresses in transit.
– Firewall Traffic Thresholds
Set firewall rules to block traffic that exceeds typical thresholds, helping detect and mitigate spoofed flood attacks.
– Security Software and Monitoring
Deploy antivirus and intrusion detection systems (IDS) to monitor for unusual activity. Continuously analyze traffic patterns and logs.
– Patch Management
Keep network devices, routers, and operating systems updated with the latest security patches to close known vulnerabilities.
– Develop and Enforce ACLs
Maintain updated access control lists defining who can access resources based on verified criteria.
IP spoofing may seem like a simple deception, but it forms the foundation of many serious cyberattacks. Whether used in large-scale DDoS campaigns or to infiltrate industrial systems, spoofed IP traffic is a persistent and growing threat. By combining packet filtering, access control, secure authentication, and continuous monitoring, organizations can dramatically reduce their exposure and improve the resilience of their industrial automation environments.
When VPNs Become a Vulnerability: The Risks of Compromised Remote Access
Traditionally, Virtual Private Networks (VPNs) have been the go-to solution for enabling remote access to internal systems. However, the explosion of distributed workforces and cloud-based infrastructure has outpaced conventional VPNs’ basic security and connectivity. As the cyber threat landscape evolves, securing your VPN has become more critical than ever.
A compromised VPN can severely weaken your cybersecurity posture, exposing IP addresses, user credentials, and sensitive data to unauthorized actors. These vulnerabilities may stem from outdated software, misconfigurations, weak encryption, or stolen login credentials. While reputable VPN providers typically offer strong protection, they are not immune to risk, especially when layered defenses are not in place.
According to Gartner, traditional VPN and jump-server-based approaches are becoming increasingly insecure and complex to manage. They often lack the granularity needed to restrict access to specific systems, instead granting broad network access. The 2024 VPN Risk Report by Zscaler and Cybersecurity Insiders found that 88% of organizations are highly concerned about potential breaches through VPN vulnerabilities.
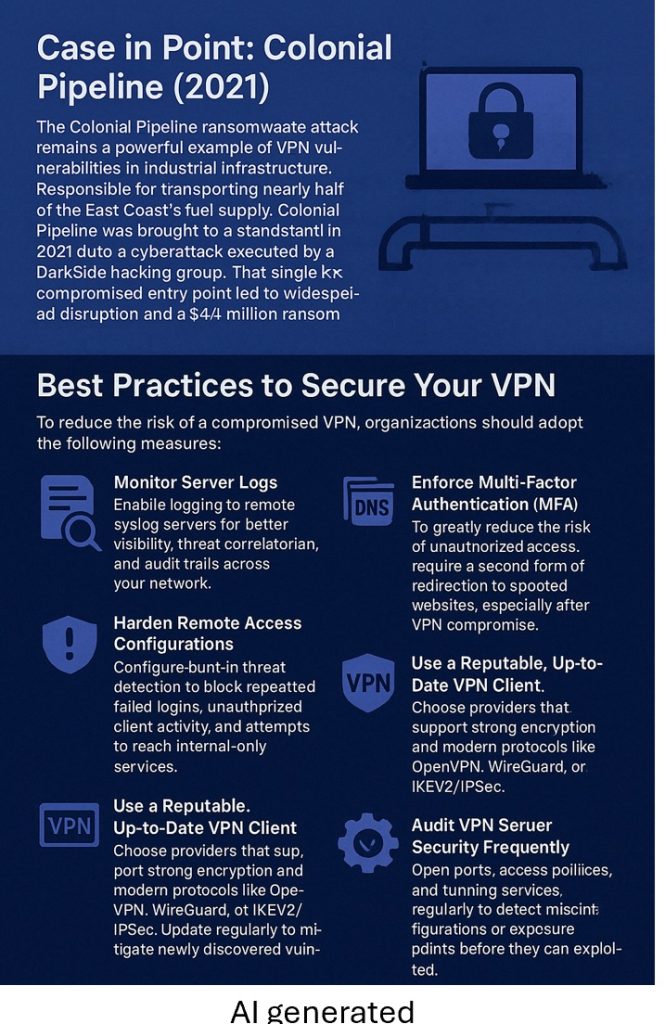
Case in Point: Colonial Pipeline (2021)
The Colonial Pipeline ransomware attack remains a powerful example of VPN vulnerabilities in industrial infrastructure. Responsible for transporting nearly half of the East Coast’s fuel supply, Colonial Pipeline was brought to a standstill in 2021 due to a cyberattack executed by the DarkSide hacking group. The attackers accessed a legacy VPN account protected by a leaked password. That single compromised entry point led to widespread disruption and a $4.4 million ransom payment in bitcoin.
Best Practices to Secure Your VPN
To reduce the risk of a compromised VPN, organizations should adopt the following measures:
– Monitor Server Logs
Enable logging to remote syslog servers for better visibility, threat correlation, and audit trails across your network.
– Harden Remote Access Configurations
Configure built-in threat detection to block repeated failed logins, unauthorized client activity, and attempts to reach internal-only services.
– Flush DNS Cache Regularly
This clears potentially malicious or outdated DNS records, reducing the risk of redirection to spoofed websites, especially after VPN compromise.
– Enforce Multi-Factor Authentication (MFA)
To greatly reduce the risk of unauthorized access, require a second form of verification (e.g., code, or biometric) in addition to a password.
– Use a Reputable, Up-to-Date VPN Client
Choose providers that support strong encryption and modern protocols like OpenVPN, WireGuard, or IKEv2/IPSec. Update regularly to mitigate newly discovered vulnerabilities.
– Integrate VPN with Endpoint Detection and Response (EDR)
– Combining VPN access with EDR monitoring provides a comprehensive view of endpoint activity and helps detect anomalies in real time.
– Audit VPN Server Security Frequently
– Open ports, access policies, and running services regularly to detect misconfigurations or exposure points before they can be exploited.
From Vulnerable Access Points to Hidden Threats
Even with a secure VPN, organizations face another growing risk: rogue devices on the network. These unauthorized or compromised devices can act as silent intruders, bypassing access controls, eavesdropping on communications, or launching internal attacks. In the next section, we will explore what rogue devices are, how they enter trusted environments, and the steps you can take to detect and defend against them.
Rogue Devices: Hidden Threats Inside Your Network
Rogue devices seriously threaten the confidentiality, integrity, and availability of your industrial and enterprise systems. These unauthorized devices, whether malicious or unintentional, can serve as entry points for malware and ransomware or even facilitate data exfiltration from otherwise secure environments. Worse yet, they often bypass traditional perimeter defenses such as firewalls, intrusion detection systems (IDS), and prevention systems, leaving a dangerous blind spot within your infrastructure.
What Is a Rogue Device?
A rogue device is any unauthorized device that connects to a network without proper approval. This could be a laptop, smartphone, USB modem, IoT device, or anything capable of network communication. While cybercriminals introduce some to carry out deliberate attacks, others are connected innocently by employees seeking convenience or productivity, such as installing a personal Wi-Fi router to extend office coverage. Both pose significant risks.
Two Types of Rogue Devices:
Black Hat Rogue Devices
Deliberately malicious and designed to steal data, disrupt operations, or spread malware.
Benign Rogue Devices
Non-malicious but unauthorized devices were added without IT approval. These still introduce vulnerabilities due to unknown or weak security settings.
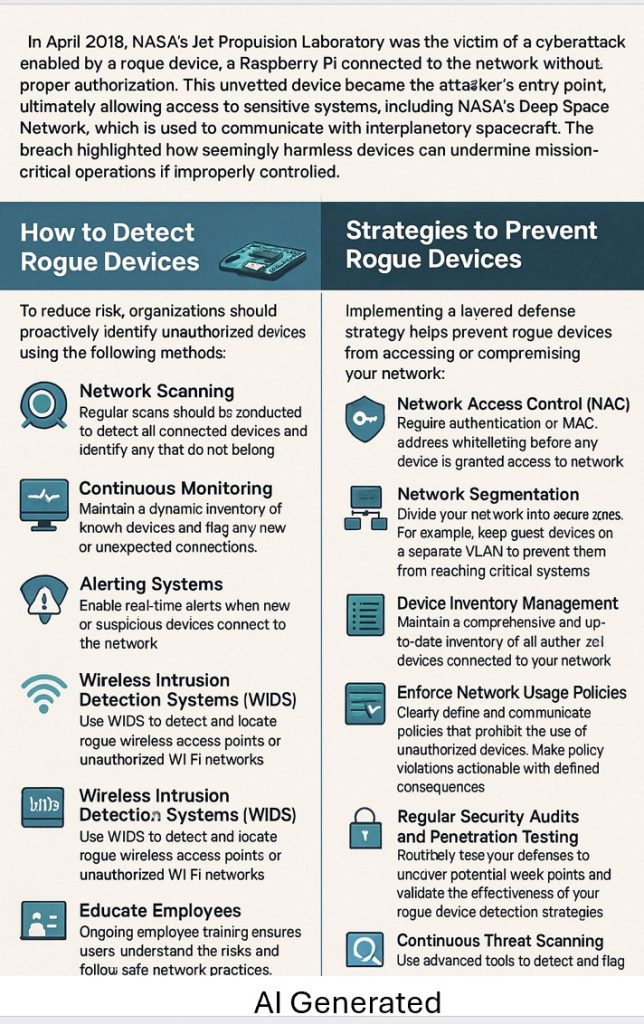
Real-World Example: NASA Jet Propulsion Lab (JPL)
In April 2018, NASA’s Jet Propulsion Laboratory was the victim of a cyberattack enabled by a rogue device: a Raspberry Pi connected to the network without proper authorization. This unvetted device became the attacker’s entry point, ultimately allowing access to sensitive systems, including NASA’s Deep Space Network, which is used to communicate with interplanetary spacecraft. The breach highlighted how seemingly harmless devices can undermine mission-critical operations if improperly controlled.
How to Detect Rogue Devices
To reduce risk, organizations should proactively identify unauthorized devices using the following methods:
– Network Scanning
Regular scans should be conducted to detect all connected devices and identify any that do not belong.
– Continuous Monitoring
Maintain a dynamic inventory of known devices and flag any new or unexpected connections.
– Alerting Systems
Enable real-time alerts when new or suspicious devices connect to the network.
– Wireless Intrusion Detection Systems (WIDS)
Use WIDS to detect and locate rogue wireless access points or unauthorized Wi-Fi networks.
Strategies to Prevent Rogue Devices
Implementing a layered defense strategy helps prevent rogue devices from accessing or compromising your network:
– Network Access Control (NAC)
Require authentication or MAC address whitelisting before any device is granted access to the network.
– Network Segmentation
Divide your network into secure zones. For example, keep guest devices on a separate VLAN to prevent them from reaching critical systems.
– Device Inventory Management
Maintain a comprehensive and up-to-date inventory of all authorized devices connected to your network.
– Enforce Network Usage Policies
Clearly define and communicate policies that prohibit the use of unauthorized devices. Make policy violations actionable with defined consequences.
– Regular Security Audits and Penetration Testing
Routinely test your defenses to uncover potential weak points and validate the effectiveness of your rogue device detection strategies.
– Continuous Threat Scanning
Use advanced tools to detect and flag unusual device behavior or unknown IP/MAC addresses.
– Multi-Factor Authentication (MFA) and Device Certificates
Strengthen access control by requiring user credentials and trusted device authentication.
– Educate Employees
Ongoing employee training ensures users understand the risks and follow safe network practices.
Conclusion:
As cyber threats grow in scale and complexity, the need for industrial automation systems to incorporate cybersecurity at every level has never been more urgent. From unauthorized remote access and VPN vulnerabilities to IP spoofing and rogue devices, today’s risks demand a layered, proactive approach that blends technology, policies, and people.
At ADISRA, we understand that secure industrial automation goes far beyond visualization and control. That is why ADISRA SmartView is engineered with modern security features, including role-based access, encrypted communication, and audit trails, designed to support secure-by-design principles. With best practices, such as multi-factor authentication, network segmentation, and secure deployment architectures, ADISRA SmartView helps safeguard your operational environment from external and internal threats.
As we continue exploring the cybersecurity landscape in our blog series, we invite you to try ADISRA SmartView.
ADISRA®, ADISRA’S logo, InsightView®, and KnowledgeView® are registered trademarks of ADISRA, LLC.
© 2025 ADISRA, LLC. All Rights Reserved.
